Network Security
Hello Everyone, and Welcome back!!
In this post, I will expand on my research in Network
Security. I will explain why information
and system security is essential for individuals and organizations. I will give an example of how the ping command
can be used as a system attack type. Also,
I will discuss in more detail phishing and social engineering. To conclude, I will add recommendations for
preventing these types of attacks. This
will demonstrate the importance of network and system security for individuals
and organizations.
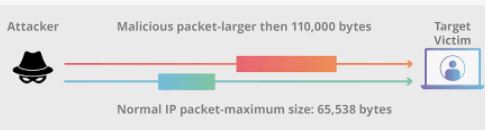
Network and system security are often not given the importance they should have. As mentioned in the scholarly article named Internet of Things: Security and Solutions Survey, “Human life is involved in enormous applications such as intelligent transportation, intelligent healthcare, smart grid, smart city, etc. A thriving surface is created that can affect society, the economy, the environment, politics, and health through diverse security threats” (Sadhu et al, 2022). Bad actors have many ways to attack an individual or organization. Bad actors can use very sophisticated to attack an individual or organization. But they can also use simple tools such as ping commands. Using the ping command, bad actors can bring a network to a halt. Using a tool such as a ping command can create what is called a denial-of-service (DoS) attack. The scholarly article Denial-of-service attack explains that “DoS attacks are typically carried out using automated programs that send repeated requests to the target site or network, thus causing the server to overload” (Crelin, 2020). Sending specially formulated packets with the ping command, an attacker can crash or make a server or computer unstable and unable to communicate; this is called the Ping of Death (PoD). One way to protect from a PoD attack is to disable the Internet Control Message Protocol (ICMP). However, that may cause unintended issues; therefore, the best way to protect from a PoD attack is to use software or a security tool that detects malformed, oversized, or suspicious pings.
A
bad actor can attack an individual or organization in many different ways. In my experience, most of the attacks I have
seen come from phishing and social engineering.
However, security should be well-rounded to prevent all types of
attacks. “Phishing is the fraudulent
attempt to obtain sensitive information by disguising oneself as a trustworthy
entity in digital communication” (Desolada et al, 2022). For a bad actor to be able to create a
dangerous and effective phishing email, it will need to do some social
engineering. As Christopher Hadnagy said
in his keynote speech at the HOPE conference, “hacking is playing with other
people and getting them to do strange things” (2018). A hacker with the right information at the
right time can be dangerous. For
example, you work in an office, which you know is your co-worker’s birthday. Suddenly you get an email from the Directory
of your department asking you if you could purchase a $100 gift card for
Freddy, not to tell anyone, and keep it secret since it will be a birthday
surprise for Freddy. He trusts you to be
able to do this simple task. Your
co-worker’s name is Freddy, it is his birthday, and the email came from your
director, or at least that’s how it looked.
The bad actor obviously did some research. By finding out publicly available information,
he was able to send a well-crafted email not only to you but to everyone in
your department. By telling everyone that
it was a secret and he trusted them, most users will not want to break that
trust. Besides, reviews are coming soon,
and you want to make sure you are on your boss’s boss good side. Although this may sound far fetch, it has
happened, and I have seen it.
The good news is that there are ways to
protect yourself and your organization against such attacks. For phishing attacks, recommendations to
protect you and your organization are as follows:
1.
Purchase
security software
2.
Educate
yourself and the users in the organization about phishing emails
The best way to protect from phishing emails is to
question everyone and trust no one. If
in question, call the sender and validate the information. Protection from social engineering is a bit
more complicated. Since the goal of an
attacker is to gain your trust, it may be difficult to see the threat. However, two recommendations to protect from
such attacks are as follows:
1.
Purchase
advanced security software
2.
Educate
yourself and the users in an organization about social engineering
Similar to the first recommendation and very
effective. Now in days, as attackers are
getting smarter, basic security software is not enough. Security
companies are turning to behavioral data science and artificial intelligence
for solutions. Security companies like
TrendMicro, and Abnormal, use Artificial Intelligence (AI) and Machine Learning
(ML) to learn the behavior of internal and external users and the relationship
between them to secure and prevent sophisticated attacks missed by conventional
spam blockers. Having sophisticated
software and educating your users can help prevent phishing and social
engineering attacks.
References:
Crelin, J. (2020). Denial-of-service attack. Salem Press Encyclopedia.
DESOLDA, G., FERRO, L. S.,
MARRELLA, A., CATARCI, T., & COSTABILE, M. F. (2022). Human Factors in
Phishing Attacks: A Systematic Literature Review. ACM Computing Surveys, 54(8), 1–35. https://doi.org/10.1145/3469886
Hadnagy, C. (2018). Social engineering : the science of human
hacking (Second edition.). Wiley.
Sadhu, P. K., Yanambaka, V.
P., & Abdelgawad, A. (2022). Internet of Things: Security and Solutions
Survey. Sensors (14248220), 22(19),
7433. https://doi.org/10.3390/s22197433
Security Abnormal. (2022, December 22). Why abnormal - email security for advanced
attacks. Abnormal Security. https://abnormalsecurity.com/why-abnormal
Vahid, F., & Lysecky,
S. (2019). Computing technology for
all. zyBooks.
What is ping of death
(pod): Ddos attack glossary: Imperva. Learning Center. (2020, September 30). https://www.imperva.com/learn/ddos/ping-of-death/#:~:text=Ping%20of%20Death%20(a.k.a.%20PoD,using%20a%20simple%20ping%20command.



Comments
Post a Comment