The OS Theory Concept Map
OS Theory Concept Map
This
final assignment will dive deeply into the Operating System Theory Concept Map.
The paper will consist of five sections,
each explaining a specific focus of the operating system. The first concept will describe features of
contemporary operating systems and their structures. The second concept discusses how the operating
systems enable processes to share and exchange information. The third concept will explain memory
management within the operating system. The
fourth concept will explain how a modern computer system handles files, mass
storage, and I/O. And the last concept
would outline the mechanisms necessary to control the access of programs or
users to the resources defined by a computer system. For each concept, I will recommend how I will
use these concepts about operating systems theory in future courses and jobs.
Concept 1: Features and structure of
contemporary operating systems
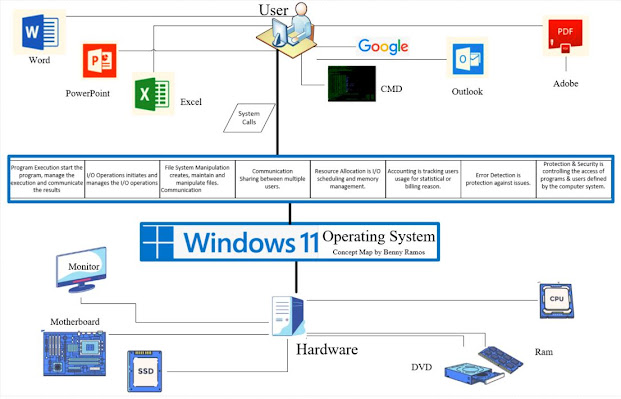
Concept number one will describe contemporary operating systems’ features and structures (See Figure 1). While the use of icons and visuals in my concept map was recognized, it failed to explain the various functions and services provided by the operating systems. The fancy visuals explain how the operating system is an intermediary between user programs, such as the command line, graphic user interface, system calls, and system hardware. I have added a set of functions and services that the operating system provides, such as program management, I/O management, and File system Management, to name a few. This section will help me quickly identify the operating system’s various services and functions. This is excellent information since I currently work in IT, and it gives me a better perspective of what happens between the user and the hardware.
Figure 1: Ramos, B.
(2023) Features and structure of contemporary operating systems [Concept
Map]
Concept 2: Threads and process
synchronization
The
second concept map is regarding threads and process synchronization. The primary keys to this concept map are the
Process, the Process Control Block, Process State, and Threads. The Process Control Block, which is also
called the task control block, consists of the following:
1. Process
state
a. New-
The process is being created.
b. Running-
Instructions are being executed.
c. Waiting-
The process is waiting for some event to occur (such as an I/0 completion or
reception of a signal).
d. Ready-
The process is waiting to be assigned to a processor.
e. Terminated-
The process has finished execution.
2.
Process number – the number to identify
any particular process
3.
Process counter – the contains the
address of instructions that needs to be executed
4.
Registers – The CPU register specifies
the register used by the process. Works
with the program counter to allow to continue the process after an interrupt.
5.
Memory limits – information used to
manage the memory. It is much dependent
on the memory used by the operating system
6.
List of open files – the list of all the
files associated with the process.
This concept map can be handy when
determining the resources needed for a program. Knowing how this works can help you choose
from single-thread to multi-thread capabilities and if issues are related to
memory limits, I/Os, and the critical-section problem and solutions. Also is good to mention that solutions to the
critical-section problem must consist of the following:
Mutual exclusion: When one process executes
in its critical section, no other process is allowed to execute in its critical
section.
Progress: When no process is executing in
its critical section, and there exists a process that wishes to enter its
critical section, it should not have to wait indefinitely.
Bounded waiting: There must be a bound on
the number of times a process is allowed to execute in its critical section
after another process has been requested.
Below is the OS Theory Concept map of Threads and process synchronization.
Figure 2: Ramos, B.
(2023) Threads and process synchronization [Concept Map]
Concept 3: Memory management
In concept map three, we will cover the memory management portion of the operating system. Memory management is the process that manages, controls, and allocates the computer’s physical memory. The CPU gives the application a logical address, which is also called a virtual address, whenever an application executes. The CPU sends the virtual address to the memory management unit (MMU) to translate the logical address into a physical address that can be put on physical memory. User address binding is a mapping of address space. This information is essential; anyone in Information Technology can benefit from it. One way I plan to use this information is to propose increasing or decreasing physical memory on servers. Knowing how each program takes a chunk of memory, I can determine that there should be a limit to how many programs can run on a single server depending on the specification of ram usage for each program.
Figure 3: Ramos, B. (2023) Memory Management [Concept Map]
Concept 4: File System, Mass Storage and
I/O
This
concept map will cover File System, Mass Storage, and I/O. There is no shortcut to explaining these three
topics. Single-Level Directory – Pros:
All files are contained in the same directory. Easy to support and understand. Cons: Difficult to scale up. Not suitable for multiple users. It must not violate the unique-name rule.
Two-Level Directory – Pros: fixes the
problem with multiple users by creating a sub-directory or user file directory
(UFD). Fixes the unique-name rule by running
programs and files under the appropriate users. Cons: Team collaboration is difficult to
implement.
Tree-Structured Directories – Pros: it
can have many sub-directories. User has
complete control over their folder and subfolder. Allow users to organize their own directory
structure under their profile. Cons:
User has complete control over their folder and subfolder, which means they can
accidentally delete important files if they don’t track their folder well. Prohibits the sharing of folders and files.
Acyclic-graph directory structure – Pros:
It fixes the problem with sharing and allows users to share folders, files, and
entire directories. More flexibility
than the previous directory structure. Cons: More complex. Links may become corrupt by deleting files. Difficult to keep track of links by adding
cycles.
General Graph Directory- Pros: It fixes
the possibility of infinite loops created by the cycles. Limits the number of directories that will be
accessed during a search. Cons: it uses
additional tools such as garbage collection to free up space.
Mass Storage and I/O refer to the ability to move data from and to memory. The hardware that allows this to happen is the motherboard with the I/O bus. In big data, SSD drives with fiber channel (FC) I/O bus is the preferred I/O hardware device to transfer data. However, because of prices, sometimes SAN storage architects use both technologies in a hybrid solution. SSD for fast data transfer and regular Hard Drives for storing data. This information and concept map is extremely useful for Systems Administrators, Engineers, and Systems Architects. The information on this concept map will be essential for designing, implementing and administrating file servers. I plan on using it while migrating our current Server 2012 environment to Server 2019. Choosing the correct storage and I/O hardware combined with a sound file structure should allow me to create a file-sharing solution for any organization.
Figure 4: Ramos, B.
(2023) File System [Concept Map]
Concept 5: Security and Protection
Security
and protection is the most critical part of the operating system. Without it, data, programs, and information
would be unsafe from unauthorized access. This information is crucial for my current job
and future goals. My goal is to obtain a
bachelor’s degree in Cybersecurity. I
will use this concept map to remind me of possible vulnerabilities in the
Operating System. Overall, the
information in this paper is essential for understanding the Operating System and
how it works.
Figure 5: Ramos, B.
(2023) Protect and Security [Concept Map]
References:
Diwan, A. (2022, August
12). Python and multi-threading is it a good idea. TutorialsPoint. Retrieved from https://www.tutorialspoint.com/python-and-multi-threading-is-it-a-good-idea#:~:text=Python%20doesn’t%20support%20multi,GIL%20does%20not%20prevent%20threading.
Dordevic, B., Timcenko, V.,
Sakic, D., & Davidovic, N. (2022). File system performance for type-1
hypervisors on the Xen and VMware ESXi. 2022 21st International Symposium
INFOTEH-JAHORINA (INFOTEH), INFOTEH-JAHORINA (INFOTEH), 2022 21st International
Symposium, 1–6. https://doi.org/10.1109/INFOTEH53737.2022.9751288
Merritt, T. (2012, December
31). Multi-threaded application vs.
Single Threaded Application - DZone. dzone.com. Retrieved February 12, 2023, from
https://dzone.com/articles/multi-threaded-application-vs
Modi, A. (2019, December
4). Java vs. python: Which should you
choose? Opensource.com. Retrieved from
https://opensource.com/article/19/12/java-vs-python#:~:text=Java%20multi%2Dthreading%20can%20support,to%20run%20at%20a%20time.
Karl-Bridge-Microsoft.
(n.d.). Processes and threads - win32
apps. Win32 apps | Microsoft Learn. Retrieved from https://learn.microsoft.com/en-us/windows/win32/procthread/processes-and-threads
Silberschatz, A., Galvin,
P. B., & Gagne, G. (2014). Operating system concepts essentials (2nd ed.). Retrieved from https://redshelf.com/
Vampugani F. (2017). Protection and security in operating
systems. Share and Discover
Knowledge on SlideShare. Retrieved from
https://www.slideshare.net/vampugani/protection-and-security-in-operating-systems-79552408
TutorialsPoint. (2021, July
28). Operating system -
multi-threading. TutorialsPoint. https://www.tutorialspoint.com/operating_system/os_multi_threading.htm
YouTube. (2021, September 27). Mem alloc algorithms: First fit, best fit,
worst fit, next fit w/ examples (English). YouTube. Retrieved from
https://www.youtube.com/watch?v=3b57mkx1rlA
Zied Milian, E., De Mesquita Spinola, M., & De
Paula Pessoa, M. S. (2015). Opportunities for strategic alignment of IT
to business with the adoption of cloud computing: Case studies in large
organizations. 2015 Portland
International Conference on Management of Engineering and Technology (PICMET),
Management of Engineering and Technology (PICMET), 2015 Portland International
Conference On, 64–74. https://doi.org/10.1109/PICMET.2015.7273067





Comments
Post a Comment